 |
| Cryptography Property Name | Details |
| Confidentiality | Information cannot be understood by anyone while in transmission. |
| Integrity | Information cannot be Modified. |
| Non-repudiation | Sender cannot deny his/her intentions in the transmission of the information at a later stage |
| Authentication | Sender and receiver can confirm each other |
Types of cryptographic techniques
| Cryptograpy Type | Details |
| Symmetric-key Cryptography | Both the sender and receiver share a single key. |
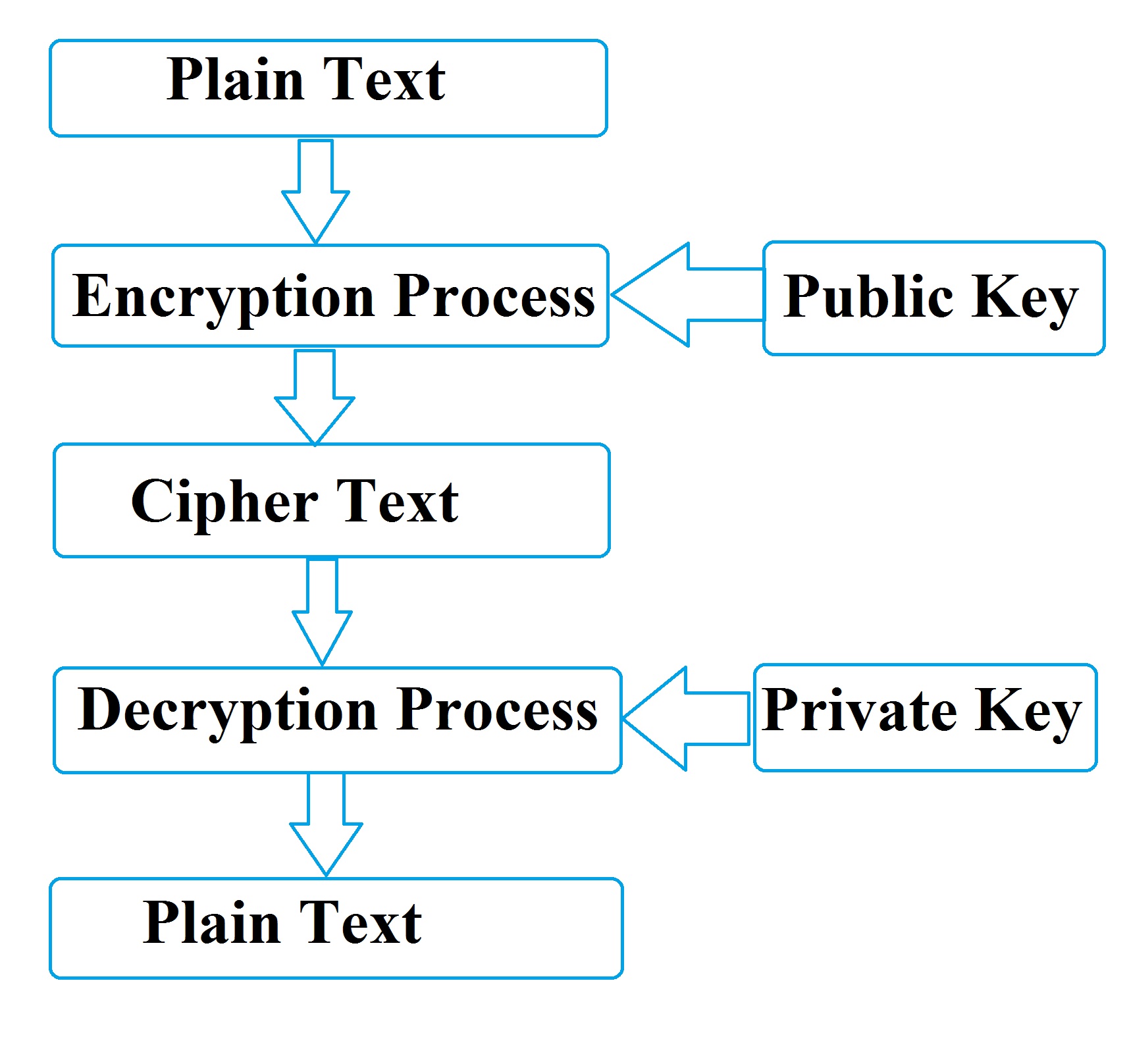
| Public-key cryptography | Here two related keys (public and private key) are used. Public key is freely distributed used for encryption and private /secret key used for decryption. |
| Hash functions. | No keys are used in this algorithm but it uses Hash functions to calculate a hash value based on plain text and its length and is used to recover plain text. |
Cryptography applications:
Banking transactions, computer passwords, Ecommerce transactions e.t.c.
Home Back